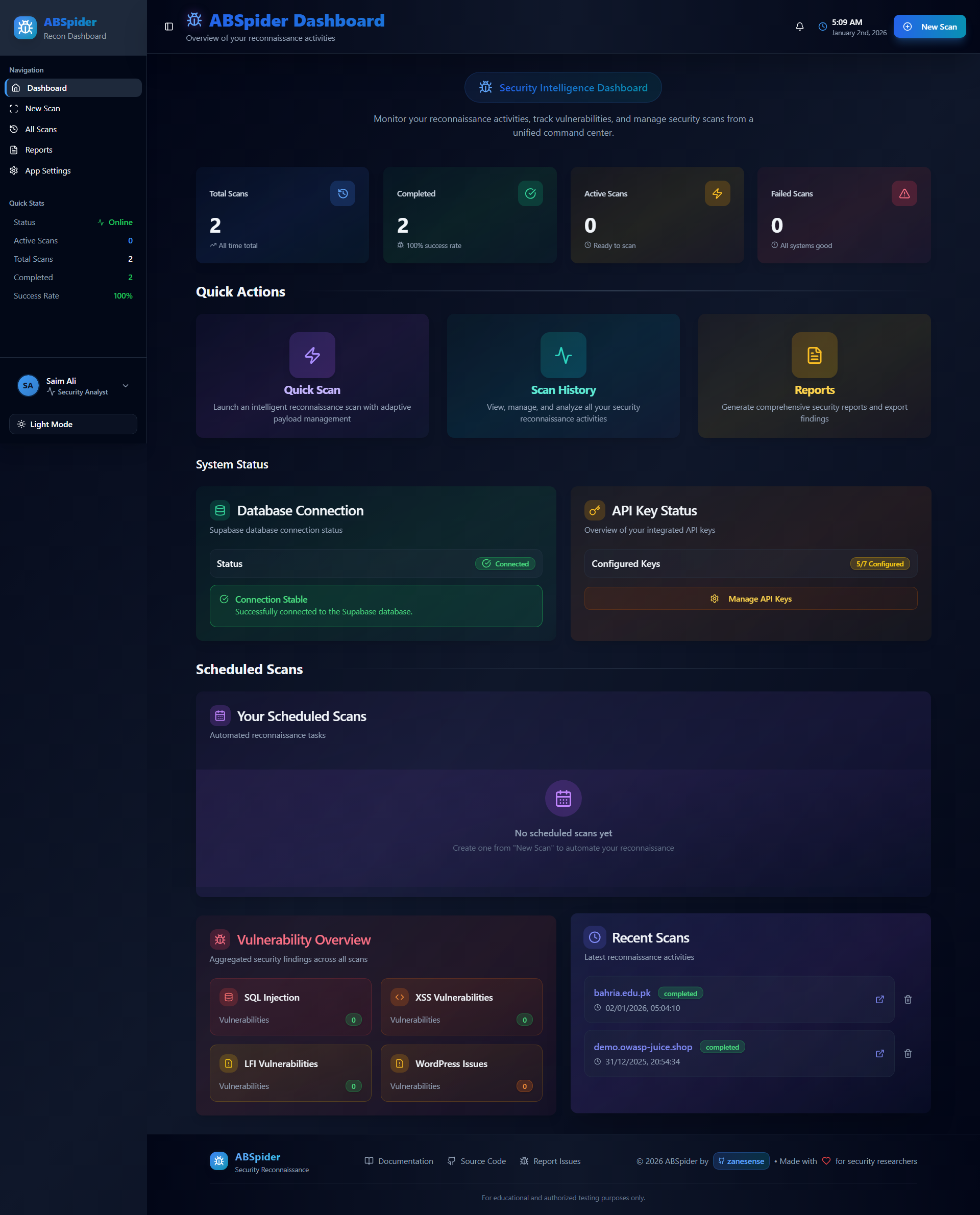
Modern Web Security Intelligence Platform
ABSpider is a powerful browser-based reconnaissance dashboard built for security professionals, penetration testers, and bug bounty hunters. Combining passive intelligence gathering with active vulnerability scanning, it delivers actionable security insights through an intuitive modern interface.
|
🚀 Zero Backend Fully browser-based |
🔒 Privacy-First Your data, your control |
⚡ 20+ Modules Comprehensive scanning |
📊 Enterprise Reports Professional PDFs |
🎨 Modern UX React + Tailwind |
🔌 Extensible Optional API integrations |
- Passive Reconnaissance: WHOIS lookup, DNS enumeration, subdomain discovery via CT logs, GeoIP location
- Active Scanning: SQL injection, XSS detection, LFI scanning, port scanning, CORS testing
- Technology Fingerprinting: Identify frameworks, CMS, analytics, and server technologies
- Security Analysis: HTTP header scoring, SSL/TLS certificate validation, WAF detection
- AI-Powered Modes: Conservative, adaptive, and aggressive scanning with intelligent payload management
- Real-time Monitoring: Target health tracking with automatic intensity adjustment
- Stealth Detection: Automatic WAF and rate-limiting detection
- Comprehensive PDF Reports: Executive summaries, detailed findings, PoC snippets, and remediation guidance
- Export Options: JSON and PDF formats for easy integration with your workflow
- Severity Scoring: Clear vulnerability classification with confidence ratings
- Notification Center: Real-time scan updates with smart categorization
- Discord Integration: Instant webhook notifications for critical alerts
- Activity Dashboard: Track scan history and performance metrics
- Centralized Settings: Manage API keys, proxies, and scan parameters from one place
- Scan Templates: Save and reuse configurations for repeated tasks
- Scheduling: Automate reconnaissance with daily, weekly, or monthly schedules
- User Profiles: Personalized preferences with role-based access
# Clone the repository
git clone https://github.com/zanesense/abspider-recon.git
cd abspider-recon
# Install dependencies
npm install
# Start development server
npm run devAccess the dashboard at http://localhost:5000
graph TB
A[ABSpider Recon<br/>React + Vite Frontend] --> B[Component Layer]
B --> B1[Dashboard UI]
B --> B2[Scan Modules<br/>20+ types]
B --> B3[Notification Center]
B --> B4[Report Generator]
B --> B5[Settings Management]
B1 --> C[State Management]
B2 --> C
B3 --> C
B4 --> C
B5 --> C
C --> C1[TanStack Query<br/>Server State]
C --> C2[React Context<br/>UI State]
C --> C3[React Hook Form<br/>Form State]
C1 --> D[Service Layer]
C2 --> D
C3 --> D
D --> D1[Scan Engine<br/>Smart Manager]
D --> D2[API Integrations]
D --> D3[Report Generation<br/>jsPDF]
D --> D4[Notification System]
D1 --> E[Supabase Backend]
D2 --> E
D3 --> E
D4 --> E
D2 --> F[External APIs]
E --> E1[Auth<br/>Magic Link]
E --> E2[PostgreSQL DB]
E --> E3[User Profiles]
E --> E4[Scan History]
E --> E5[Settings]
E --> E6[API Keys]
F --> F1[Shodan]
F --> F2[VirusTotal]
F --> F3[SecurityTrails]
F --> F4[Hunter.io]
F --> F5[CT Logs]
F --> F6[DNS APIs]
F --> F7[WHOIS/RDAP]
style A fill:#4F46E5,stroke:#312E81,stroke-width:3px,color:#fff
style B fill:#7C3AED,stroke:#5B21B6,stroke-width:2px,color:#fff
style C fill:#EC4899,stroke:#BE185D,stroke-width:2px,color:#fff
style D fill:#F59E0B,stroke:#D97706,stroke-width:2px,color:#fff
style E fill:#10B981,stroke:#059669,stroke-width:2px,color:#fff
style F fill:#06B6D4,stroke:#0891B2,stroke-width:2px,color:#fff
Frontend Framework
- React 18 with Vite for blazing-fast HMR
- TypeScript for type safety
- Tailwind CSS + shadcn/ui for modern UI
State & Data Flow
- TanStack Query for server state and caching
- React Context for global app state
- React Hook Form + Zod for form validation
Backend & Storage
- Supabase Auth (passwordless magic link)
- Supabase PostgreSQL for user data & scan results
- Row-level security for data isolation
Scanning Engine
- AI-powered payload management
- Adaptive rate limiting
- Multi-threaded execution
- Real-time health monitoring
Reporting & Notifications
- jsPDF + jspdf-autotable for PDF generation
- Discord webhook integration
- In-app notification center
- Sonner for toast notifications
| Module | Description | Type |
|---|---|---|
| 🌐 Site Info | IP, server, CMS, robots.txt analysis | Passive |
| 🛡️ Headers | Security header scoring (HSTS, CSP, XFO) | Passive |
| 📜 WHOIS | Domain registration and ownership data | Passive |
| 📍 GeoIP | Server location identification | Passive |
| 📡 DNS | A, AAAA, CNAME, TXT, MX, NS records | Passive |
| 🔍 Subdomains | CT log enumeration and DNS discovery | Passive |
| 📈 SEO | Meta tags, headings, performance analysis | Passive |
| 🔌 Ports | Service detection with Shodan integration | Active |
| 💉 SQLi | SQL injection vulnerability testing | Active |
| ✍️ XSS | Reflected, DOM, and stored XSS detection | Active |
| 📁 LFI | Local file inclusion scanning | Active |
| Cross-origin misconfiguration testing | Active | |
| 🦠 VirusTotal | Domain reputation and malware scanning | Active |
| 🔒 SSL/TLS | Certificate validation and analysis | Passive |
|
🎯 Bug Bounty Hunters Rapid reconnaissance and vulnerability discovery |
🛡️ Penetration Testers Comprehensive security assessments with professional reporting |
🔍 Security Researchers Deep-dive analysis of web application architecture |
|
📋 Security Auditors Compliance testing and security posture evaluation |
🚨 Red Team Operations Initial footprinting and attack surface mapping |
👨💻 Developers Security testing during development lifecycle |
- Supabase Authentication: Passwordless magic link login
- Role-Based Access: Secure user management and permissions
- Data Encryption: Client-side storage with secure handling
- API Key Management: Optional integrations with Shodan, VirusTotal, SecurityTrails, and more
⚠️ Security Notice: API keys are stored client-side. Use test keys only—never production or sensitive credentials.
- Only scan systems you own or have explicit written permission to test
- Unauthorized scanning is illegal in most jurisdictions
- You are solely responsible for compliance with applicable laws (CFAA, GDPR, etc.)
- Keep documentation of authorization for all scans
- Violations may result in criminal prosecution, fines, and civil liability
This tool does not grant permission to scan any system.
- Frontend: React + Vite + Tailwind CSS + TypeScript
- UI Components: shadcn/ui + Lucide Icons
- Backend: Supabase (Auth & Database)
- Reports: jsPDF + jspdf-autotable
- State Management: TanStack Query
- Forms: React Hook Form + Zod
- Multi-target batch scanning
- Custom payload libraries
- Advanced WAF fingerprinting
- Automated vulnerability chaining
- Integration with popular security tools (Burp Suite, OWASP ZAP)
- Mobile app for iOS/Android
- Team collaboration features
- Backend API for enterprise deployments
Q: Do I need API keys to use ABSpider?
A: No! ABSpider works out-of-the-box with passive modules. API keys are optional for enhanced features (Shodan, VirusTotal, etc.).
Q: Is this legal to use?
A: Yes, but only on systems you own or have explicit written authorization to test. Unauthorized scanning is illegal.
Q: Can I use this for commercial projects?
A: Yes! ABSpider is MIT licensed. You can use it for both personal and commercial purposes.
Q: Does ABSpider store my scan data?
A: Scan results are securely stored in your Supabase database and associated with your account. Your data is private and accessible only to you.
Q: How accurate are the vulnerability findings?
A: Results include confidence scores. Always manually verify findings before reporting vulnerabilities.
Q: Can I contribute to the project?
A: Absolutely! Check our contribution guidelines.
- 📖 Full Documentation (Coming Soon)
- 🐛 Report Bugs
- 💡 Request Features
- 💬 Discussions
Contributions are welcome! Check out our contribution guidelines to get started.
This project is licensed under the MIT License - see the LICENSE file for details.
Built with 💜 by zanesense
Empowering security professionals worldwide 🚀